Two-factor authentication (2FA) significantly boosts security for user logins in ioGates, providing an additional layer of protection beyond just the username and password. This feature is particularly recommended for safeguarding sensitive content.
Setting Up 2FA for User Logins
-
Administrator Access Required:
Only account administrators have the privilege to activate 2FA for user logins. This ensures that the implementation of such security measures is controlled and deliberate. -
Activating 2FA:
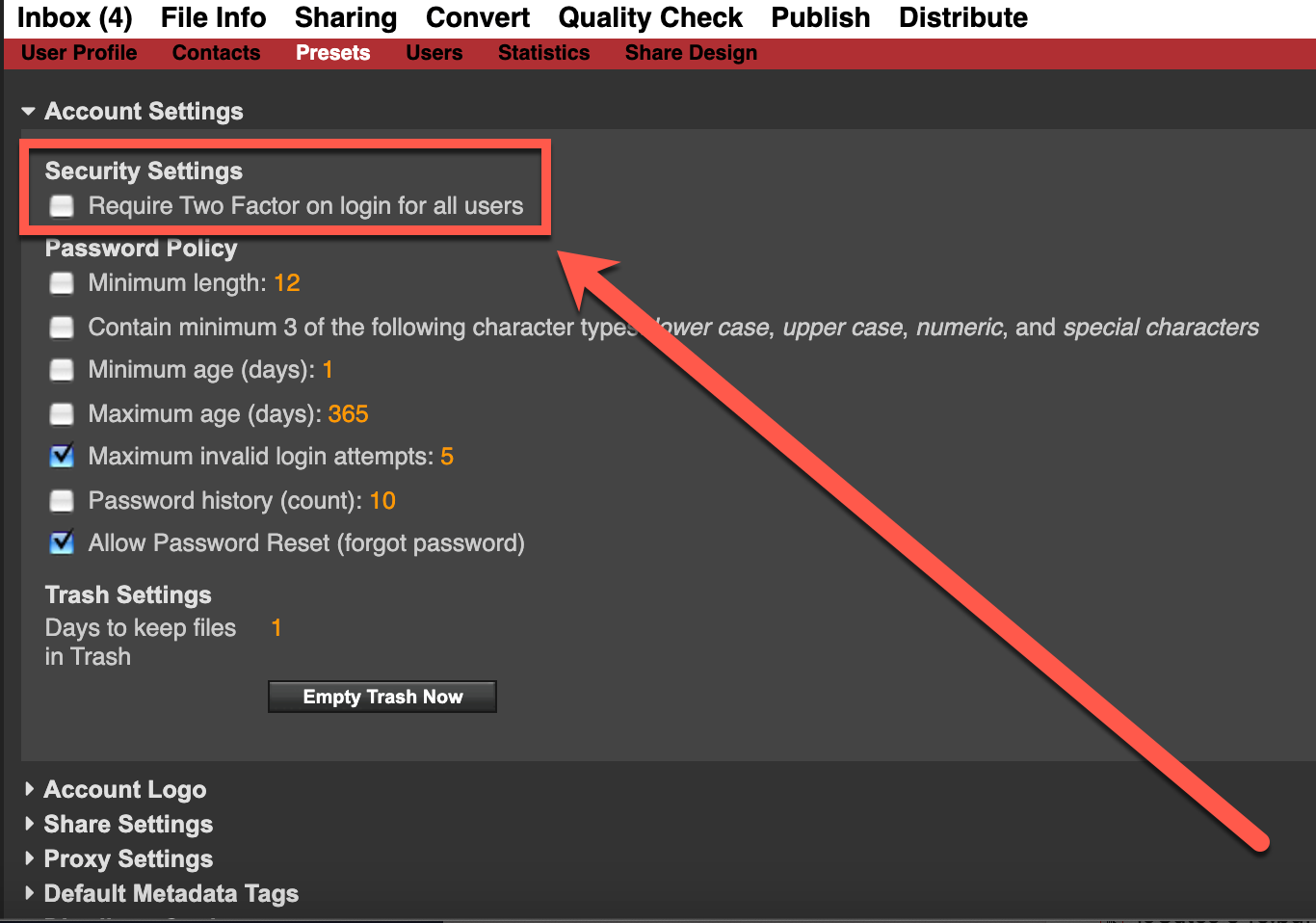
- Navigate to the Preferences menu within your ioGates account.
- Locate and select the option “Require SMS access token on login.” This action enables 2FA for all users associated with the account.
-
Verifying Phone Numbers:
- Upon activation, ioGates will prompt users to verify their cell phone numbers. A code will be sent via text message to the provided number, which users must enter into a pop-up window to complete the verification process.
- It's crucial to ensure that every user associated with the company's ioGates account has a valid cell phone number entered into their user profile to facilitate the 2FA process.
Importance of 2FA for User Logins
- Enhanced Security: 2FA adds a critical security layer, making it significantly harder for unauthorized individuals to gain access to your ioGates account, even if they manage to obtain a user's password.
- Reduced Risk of Unauthorized Access: By requiring something the user has (their phone) and something the user knows (their password), 2FA drastically reduces the risk of compromised accounts.
- Best Practice for Data Protection: Implementing 2FA is considered a best practice in the industry, particularly for platforms handling sensitive or proprietary information.
Implementation Considerations
Before enabling 2FA, administrators should communicate with all users to ensure they understand the new login process and verify that accurate cell phone numbers are recorded in ioGates. This preparatory step is essential to avoid access issues post-implementation.